
Your Security. Our Priority.
Trusted by the DoD and DOE, Legion is built on zero trust principles, enforcing data sovereignty, fine-grained access controls, and CVE-hardened deployments to keep your data secure as you turn it into better, faster decisions.
How Legion secures your data

Secure by Default
Legion was built from the ground up to protect sensitive data, enforce zero-trust boundaries, and maintain full data sovereignty in even the most classified environments.

Control with Clarity
Granular controls and deep observability give admin teams full visibility into what both humans and AI can access, what they’re doing, and who’s authorized to use it.

Flexible by Design
Legion adapts to your infrastructure, not the other way around - we deploy in any environment while preserving security, compliance, and control.


Ensure Privacy and Compliance for Government and Enterprise
 HIPAA
HIPAA GDPR
GDPR SOC 1 Type 2
SOC 1 Type 2 SOC 2 Type 2
SOC 2 Type 2- IL2–6
- CMMC
Secure by Default
You Control Where Your Data Goes
All AI processing happens within your environment - no model training & no data exfiltration.
Efficient, Secure Context Sharing
Legion mediates between your data and the LLM - sharing only what’s needed to resolve the query, and nothing more.
Least Privilege, Enforced
Each assistant, model, and integration operates with its own scoped permissions, never assuming implicit access.
Control with Clarity
Fine-Grained Access Policies
Configure access to data, models, and tools at the user, group, or role level - ensuring secure operations aligned to mission requirements.
Platform-Wide Telemetry
Monitor model and token usage, data interaction, and product usage analytics with real-time logging and reporting across deployments
Governable by Default
Enforce operational guardrails, define resource prioritization, and retain full administrative control without sacrificing speed or flexibility.
Flexible by Design
Deploy in High-Security Environments
Support for on-prem, VPC, air-gapped, or bare metal - even in highly secure environments (IL-2 through IL-6).
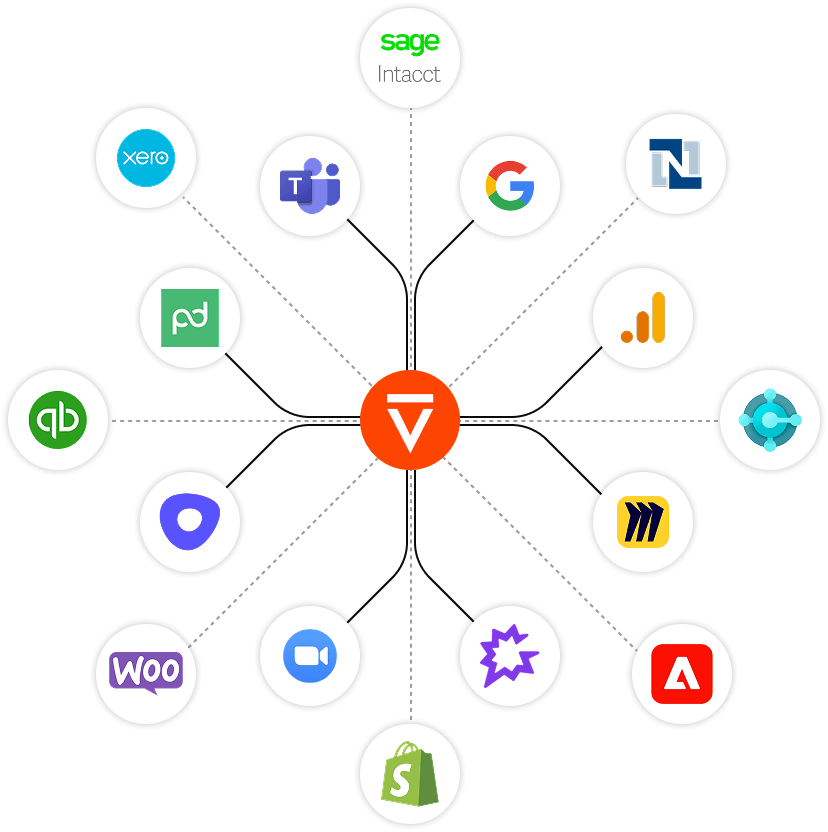
Seamless, Secure Integrations
Connect to 100+ enterprise systems while keeping data residency and identity controls intact.
Built to Evolve
Adapt your stack as needs change - every component is modular, policy-controlled, and deployed with security isolation at its core.

FAQs
Get a DemoHow is my data kept secure within the Legion platform?
Legion uses a multi-layered security approach. Data in transit is encrypted with TLS protocols, and data at rest is protected with AES-256 encryption in secure, access-controlled repositories. It maintains complete data sovereignty through a secure middle-man architecture between your data and LLMs. Your information never leaves its environment, is never used to train AI models, and remains under your control at all times.
Legion is secure enough for federal agencies, as evidenced by its deployment in US Department of Defense and Department of Energy environments. The platform is SOC2 Type 1 & 2, GDPR, HIPAA, and CMMC Type 2 Level 1 compliant and supports secure deployment options including:
- On-premises
- Hybrid environments
- Private Cloud
- Air-gapped networks
- IL-2 through IL-6 (Classified SECRET) environments
What measures are in place to control and monitor access to my data?
Legion provides comprehensive access control and monitoring through:
- Role-based access control (RBAC) for secure user management
- Single Sign-On (SSO) and Multi-Factor Authentication (MFA) for secure access
- Granular administrative controls at document, agent, and model levels
- Permission-based access by role, group, or individual user
- Real-time metrics and performance dashboards for monitoring activity
- Rate limiting and token-based quotas to control usage and prevent undetected exfiltration by limiting the amount of data being processed
Legion's architecture gives administrators complete visibility into resource allocation, prioritization, and compute management. The platform ensures users only access data they're authorized to see, maintaining strict data sovereignty while providing administrators the tools to monitor and control all system interactions.
Additionally, rate limiting and quotas are designed not only to manage usage costs but also to enhance security by preventing excessive or anomalous data processing activities.
These controls operate within Legion's secure middle-man architecture that prevents any data from leaving your environment or being used to train external models.
How do you collect, store and use the data input into the Legion platform?
We only collect the minimum data necessary to provide our AI-powered services. This typically includes the queries and documents you input for analysis. We do not collect any extraneous user data. All collected data is securely stored and used solely to process your requests and improve our models, never for any other purpose.
Who owns the IP of the outputs generated by Legion Intelligence?
You maintain full ownership of any data you input into our system as well as the outputs generated using that data. We claim no intellectual property rights over your data or the insights and content our AI generates for you. Your data is not used to train our general models without express consent.
What third parties, if any, have access to the data I put into the Legion platform?
Your data is never shared with any third parties without your explicit permission. The only exception is if you opt to use third-party AI models or APIs in conjunction with our platform. In that case, the data is shared only to the extent necessary to process your request.
How can I monitor and audit the way my data is being used?
Our platform includes built-in tools for data governance and auditing. You can view detailed logs of all data access and usage through your admin dashboard. We can also provide periodic usage reports and work with your team to set up automated monitoring and alerts.
What relevant security and privacy certifications does Legion maintain?
Legion is GDPR, SOC1 Type 2, SOC2 Type 1 & 2, HIPAA, and CMMC Type 2 Level 1 compliant, and has been approved for use in secure environments IL-2 through IL-6 (Classified SECRET).
Legion is trusted by the US Department of Defense (DoD) and Department of Energy (DoE), demonstrating its ability to meet high security standards.
Legion's development practices leverage DISA strict security guidelines to create highly secure software that meets stringent security requirements, which helps shorten approval times for government deployments.
How does Legion prevent users from accidentally sharing sensitive data, such as CUI sensitive data, when using a collection?
Legion includes robust access controls for collections to safeguard sensitive data. Internal and Internet calls are kept separate, ensuring that internal data is not exposed to the internet.
Additionally, Legion can display a banner indicating CUI data to raise awareness and prevent accidental exposure. These measures help maintain the security and confidentiality of your data.

